Active Reconnaissance is the method of gathering information directly from the targets. Be aware, This information gathering method may get logged by IDS, IPS, and EDR.
DNS Enumeration
Sn1per
This is a tool to use other open source tools for automated information gathering.
Download Sn1per.
Zone Transfer
If zone transfer is misconfigured, all address will be discovered
host -l ns google.com
dnsrecon -d microsoft
Discover Subdomain
dnsenum -f namelist.txt microsoft.com
sublist3r -o output.txt -d microsoft.com
amass enum -active -d microsoft.com -ip -dir microsoft -src -brute
Check every discovered subdomain manually.
Host Enumeration
Attackers find live hosts, open ports, os version,services running, etc. Two tools can be used effectively.
Nmap Scanning
It is the most popular port scanner and also can identify OS, Live hosts, etc.
Nmap Switch
| Switch | Description |
|---|---|
-Pn |
No ping scan, useful when target does not allow pinging |
-sS |
Syn Scan |
-sU |
UDP Scan |
--open |
Only display open ports |
-A |
Aggressive Scan(OS and Software Version Detection, Script Scanning, Traceroute) |
-O |
Detect OS version |
-sV |
Enumerate Software version |
-sC |
Also run default nmap scripts to find vulnerability |
-p 1-65535 |
Scan All ports |
-p- |
Scan All ports(Short version of -p 1-65535) |
-T1 |
Slow Scan |
-T2 |
Normal Speed Scan |
-T3 |
Parallel, Normal speed scan |
-T4 |
Parallel, Fast scan |
-oN nmap.txt |
Save output to nmap.txt |
-iL |
Scan list of ip from a text file |
Identifying Live Hosts
nmap -sn -oN nmap.txt 192.168.100.0/24
Scan IP List From File
If we have some target ips in text file.
nmap -v -oN nmap.txt -iL target.txt
Simple/Basic Scan
Scan for top 1000 ports
nmap -v -oN nmap.txt 192.168.100.10
Aggressive Scan
Aggressive Scan all ports, also detect OS, Services, Script scanning, and Traceroute
nmap -A -p- -oN nmap.txt 192.168.100.10
Detect OS Version
Aggressive Scan all ports without sending ICMP request
nmap -O -oN nmap.txt 192.168.100.10
Detect Software Version
Scan ports, also Detect the Service version
nmap -sV -Pn -oN nmap.txt 192.168.100.10
Run Default Scripts
Run default scripts to find common vulnerabilities
nmap -v -sC -oN nmap.txt 192.168.100.10
Stealth Port Scan
Decoy and Spoof Mac
nmap –D 192.168.100.11, 192.168.100.102,192.168.100.101 --spoof-mac 192.168.100.10
Stealth Scan
nmap -sS -O --max-retries 1 microsoft.com
Few ports in a Subnet
Attacker usually will not start scanning all ports at the beginning. They will try to find some common ports such as 80,443,8080 and some others.
nmap -sS -sV -Pn -O -p80,443,8080,22 192.168.100.0/24
Port Scan Using Netcat
Scan ports
> nc -zvn 192.168.88.172 21-100
(UNKNOWN) [192.168.88.172] 80 (http) open
(UNKNOWN) [192.168.88.172] 22 (ssh) open
Scan a ip lists from file:
while read targets; do nc -v -z $targets 1-65535; done < ips
Manually connect to ports, if it is open, grab the banner
> nc -vvv 192.168.100.10 80
192.168.100.10: inverse host lookup failed: Unknown host
(UNKNOWN) [192.168.100.10] 80 (http) open
GET / HTTP/1.1
HTTP/1.1 400 Bad Request
Date: Sat, 19 Mar 2022 19:28:33 GMT
Server: Apache/2.4.53 (Debian)
Content-Length: 301
Connection: close
Enumerate SMB
smbmap -H 192.168.100.10
enum4linux -U -o 192.168.100.10
Enumerate SSH
msf6> use auxiliary/scanner/ssh/ssh_version
ssh [email protected]
Enumerate HTTP/HTTPS
If target host running http/https, Then must be carefully tested for web vulnerabilities. Web pentesting documented in details in Web Pentest Section. Every subdomain, web pages, input point should be tested!
Enumeration Unknown Services
The target host might be running some service we don’t have any knowledge about. For such a situations basic enumeration could be like
- Use nmap on that port
- Use Netcat to grab the banner
- Search for that port/services.
- Search for more information using discovered info.
nc -vvv target.com 1337
WH*AT <return><return>
Some more enumeration technique documented Here.
Vulnerability Assessments
If we have done the enumeration correctly and have enough data, we actually can search for vulnerability manually. It could be time consuming, But yeah, the bad hacker take their enough time. If we want more faster result we can use some automated tools to find vulnerability.
Note: All automated finding should be tested manually!
Nmap
Nmap can be used for vulnerability scanning too.
nmap --script-updatedb
nmap -T4 -A --script all 192.168.100.10
Nessus
Most popular vulnerability scanner.
1st, Click on Create a new scan
2nd Select Advanced Scan
3rd, Click on Discovery in the sidebar Menu and Turn off Ping The Remote Host
If it is Internal testing or if have the credential we can provide it on, Credentials Tab
4th, In default all plugins are enabled. But we don’t want that, because we know the OS is Debian Based Linux. So we should select the appropriate plugins
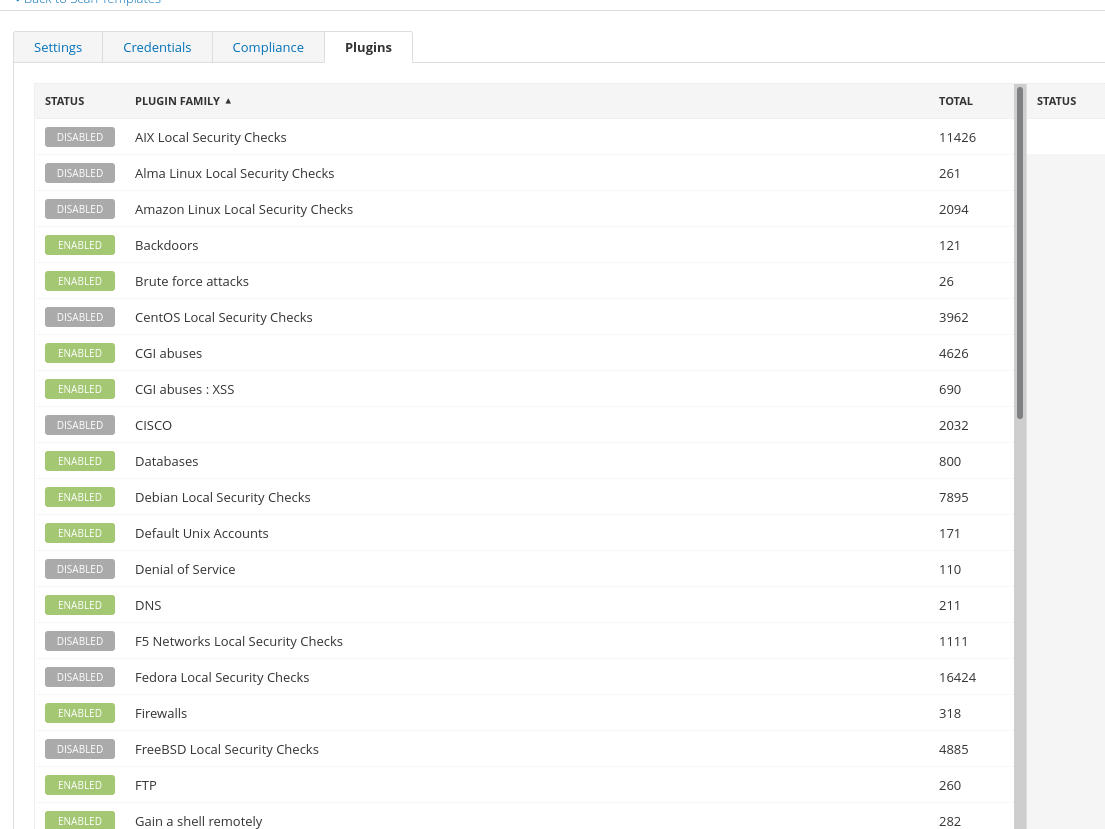
Now save and start scan!
Note: Using Nessus we can also scan for web vulnerability.
Identifying Web Vulnerability
If we have found a web server, it should be carefully analyzed for vulnerability.
Nikto
Popular and open-source vulnerability scanner. It usually search for misconfiguration, software version, dangerous files. Does not look for vulnerability like SQLi or RCE .
nikto -h http://192.168.100.10
Gobuster
Usually used to brute force for files and directories
gobuster dir -u http://host/ -t 15 -w /usr/share/dirb/wordlists/common.txt -x .php,txt,conf
Every new directory should be brute forced!
Wpscan
A popular wordpress enumeration and vulnerability scanner
wpscan -e vp --plugins-detection aggressive --api-token API_KEY --url http://172.31.1.8
Burp Suite Pro
If commercial, Then this is the first choice! :)
- Intercept all request through burp proxy
- Discover all contents
- Select the suspicious url from
Target→Site map> Scan
TIPS
Goal is do everything without getting detected. There are high possibility to get detected if we perform Active Information Gathering or Vulnerability Scanning which is not so efficient. But if we still need to scan the target
- Use Proxy/VPN
- First Try Manual testing with minimum requests.
- Avoid scanning entire site
- Only do slow scan
- Only scan suspicious urls
Also, Have a look at This Pentesting Cheatsheet